If you are searching for a brief description of JWT then this blog might help you a lot. Let's jump into it!
Overview
Hello folks👋, This is a mini blog series where we learn core things about JWT with a real-world project. In the first sequel, We will scrape the theory part and In the second sequel, We will implement the stuff that we learned in the first part in a real-world project. After the end of this series, You will have a clearer view and understanding of JWT which helps you to build a top-notch(advanced and secured) authentication system in your real-world project.
So, In this first part, We will discuss about the core stuff about JWT. Let's get started🤩
Quick Look
To increase your interest and excitement, I will showcase what wanna we will build by the end of this series.
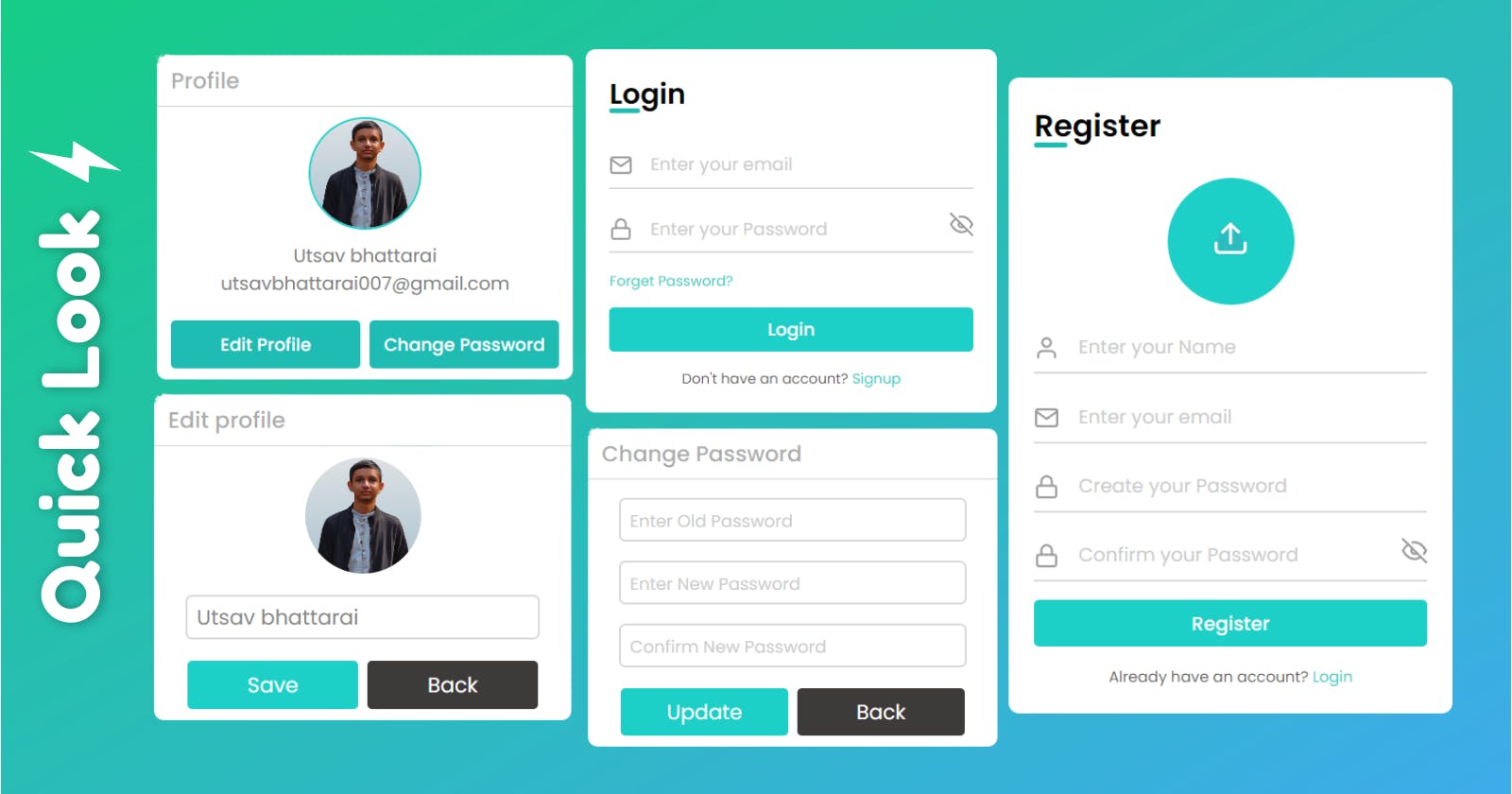
This is just a piece of work. We will build a good-looking and functional real-world project.
What is JWT(Json web token)?
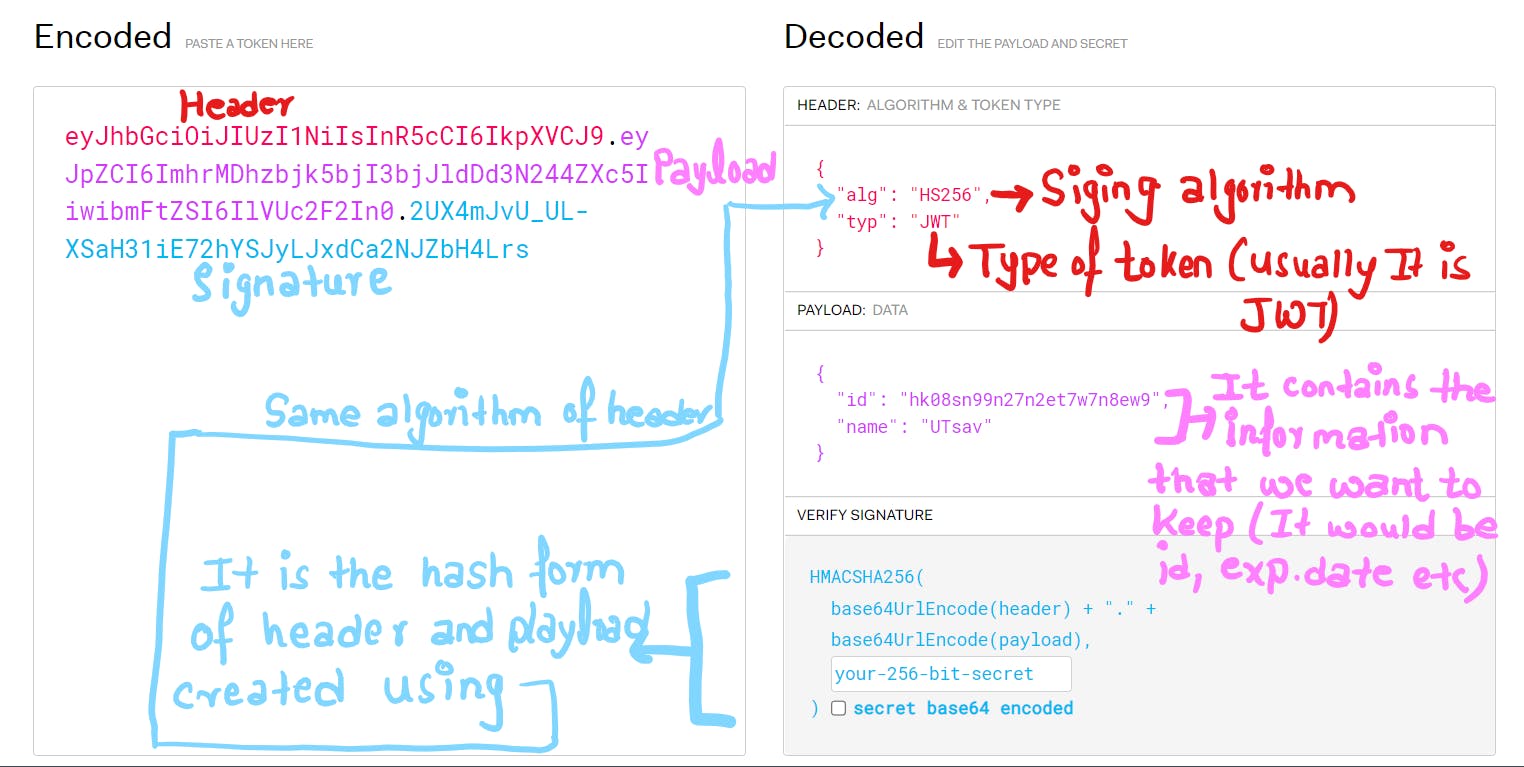
A JSON web token(JWT) is JSON Object which is used to securely transfer information over the web(between two parties). It can be used for an authentication system and can also be used for information exchange. The token is mainly composed of a header, payload, and signature. These three parts are separated by dots(.) and represented by
[header].[payload].[signature]
- Header -> It specifies the algorithm used to encrypt the contents of the token
- Payload -> It contains “claims” (information the token securely transmits)
- Signature -> It s used to verify the authenticity of the information.
Structure of JWT
Uses of JWT
- Authentication: When a user successfully logs in using their credentials, an ID token is returned which helps to authenticate the user in the future. The best and most secure way to use JWT in authentication is by using both access and refresh tokens.
Access token: It is a short-term JWT token that is used in the header to request the server for authentication, getting access to a protected route, or accessing the resources.
Refresh token: It is a long-term JWT token that is used to get a new access token when the old access token is expired.
The combo use of the Access token and Refresh token provides secure authentication and seamless user experiences which We will doing in our real project.
Authorization: Once a user is successfully logged in, an application may request to access routes, services, or resources (e.g., APIs) on behalf of that user. To do so, in every request, it must pass an Access Token, which may be in the form of a JWT.
Information exchange: JWTs are a good way of securely transmitting information between parties because they can be signed, which means you can be sure that the senders are who they say they are. Additionally, the structure of a JWT allows you to verify that the content hasn't been tampered with.
What is JWT authentication?

JWT authentication is a token-based stateless authentication mechanism. It is popularly used as a client-side-based stateless session, this means the server doesn’t have to completely rely on a data store (or) database to save session information. The client of this token may use this digital signature to demonstrate ownership in the future. Signed tokens can be used for authentication by verifying the genuineness of the claims they are attached to.
How does JWT authentication work?
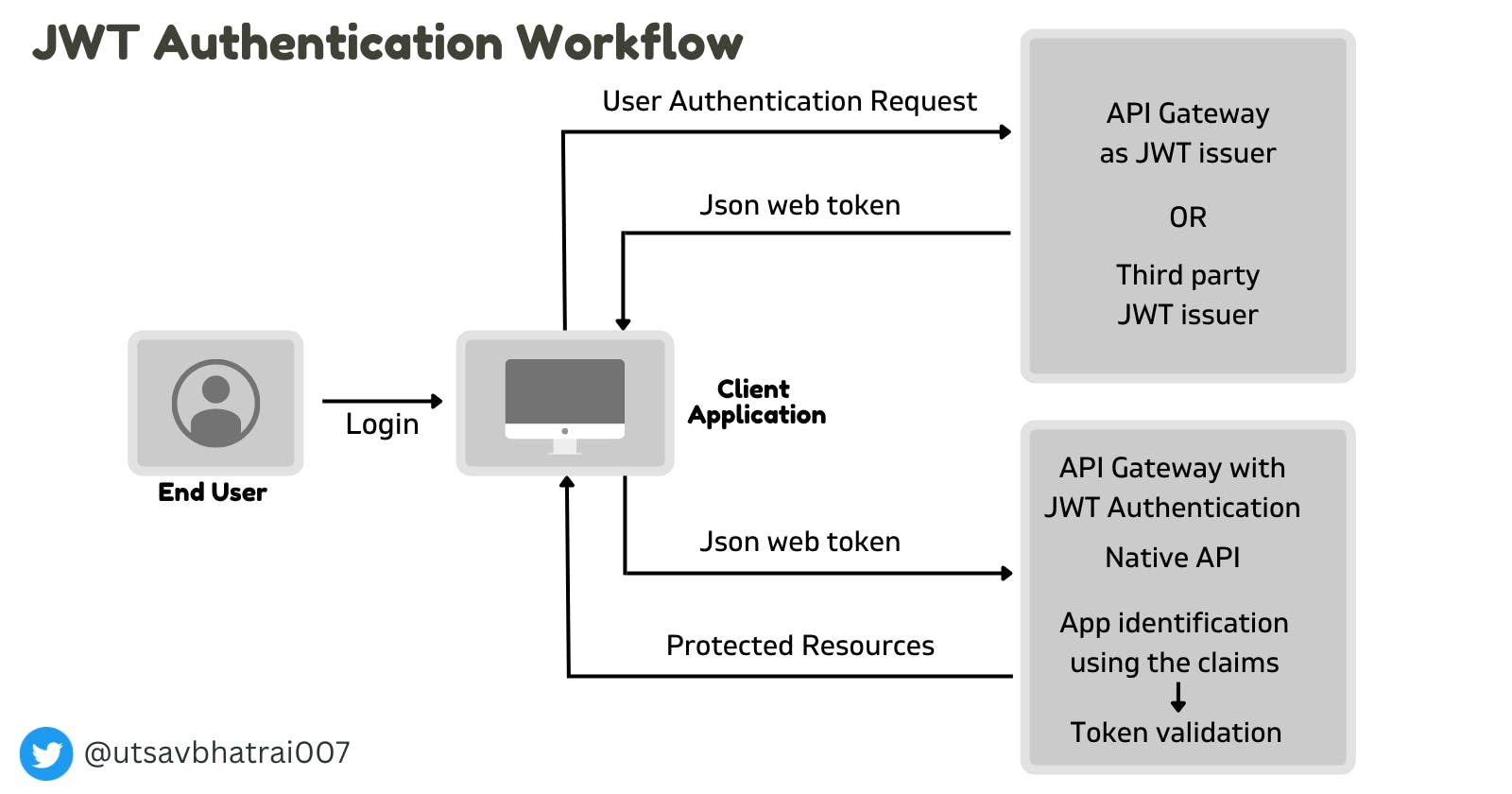
At first, The User sign-in using a username and password.
The authentication server verifies the credentials and issues a JWT signed using a private key.
Moving forward, the client will use the JWT to access protected resources by passing the JWT in the HTTP Authorization header.
The resource server then verifies the authenticity of the token using the public key.
The Identity Provider generates a JWT certifying user identity, and the resource server decodes and verifies the authenticity of the token using the public key.
Since the tokens are used for authorization and authentication in future requests and API calls great care must be taken to prevent security issues. These tokens shouldn’t be stored in publicly accessible areas like the browser’s local storage or cookies. In case there are no other choices, then the payload should be encrypted.
Benefits of JWT

The benefits are:
1. More compact
JSON is less verbose(long) than XML, so when it is encoded, a JWT is smaller than a SAML token. This makes JWT a good choice to be passed in HTML and HTTP environments.
2. More secure
JWTs can use a public/private key pair in the form of an X.509 certificate for signing. A JWT can also be symmetrically signed by a shared secret using the HMAC algorithm.
3. More Common
JSON parsers are common in most programming languages because they map directly to objects. This makes it easier to work with JWT.
4. Easier to process
JWT is used at the internet scale. This means that it is easier to process on user's devices, especially mobile.
Attack against JWT

1. Tampering with the Signing Algorithm:
‘none’ algorithm: JWT supports the usage of ‘none’ algorithm for use-cases where the integrity of the claim within JWT is already verified by other means. This algorithm allows the server to issue a JWT without a signature. The content within a token issued with a ‘none’ algorithm will look like the following:
{"alg":"none","typ": "JWT"}.{"sub":"1234567890","name":"John Doe","iat": 1516239022}.
Attackers can use this feature to set the algorithm in their token to ‘none’ and provide an empty signature to fool the server into accepting it as a valid token.
2. Brute-Forcing HS256:
JWTs signed with HS256 algorithm could be vulnerable to secret-key disclosure. that usually happens through brute-force attacks, especially for weak keys. Since a client does not need to interact with the server to check the validity of secret key after a token is issued by the server, attackers can conduct offline brute-force attacks against the token by using wordlists of possible secret keys.
3. Sensitive Information disclosure:
All the information inside the payload is stored in plain text. It is important not to leak sensitive information such as internal IP addresses through the tokens.
Attacks against JWT arise from bad implementations and using outdated libraries. To benefit from the security features JWT offers, follow the best practices for implementing them, only use up-to-date and secure libraries and choose the right algorithm for your use-case.
Connect me through👉@utsavbhatrai007
Thanks for Reading💖